Intel TCC Tools - Get Started¶
Attention
- Intel® Time Coordinated Tools Update: January 13th, 2023
In 2021, Intel® Time Coordinated Computing (TCC) was launched to the market with the 11th Generation Intel® Core™ Processors and Intel Atom® x6000E Processors to strong interest from customers and ISVs looking to deploy time sensitive applications on Intel platforms. The deep engagements with these partners have provided key learnings and insights on how to optimize our overall offering. Based on these learnings, we are making changes to our Intel® TCC offering in 2023 to optimize and simplify the experience.
- What is not changing:
The overall HW and SW capabilities of Intel® TCC and its availability to customers remains unchanged and will continue to be offered on multiple current and future platforms. This includes cache optimizations such as Cache QoS and Cache Allocation Technology (CAT), streams optimizations, such as Virtual channels, TCC BIOS mode, Real Time Compute Performance (RTCP) application and KPI result, and many more. For more information on Intel® Time Coordinated Computing, please see Intel® Time Coordinated Computing.
- What is changing:
Intel® TCC Tools, an add-on package of tools and libraries, including Data Streams Optimizer (DSO) and SWSRAM components, will no longer be offered. The changes will apply to future platforms starting with 13th Generation Intel® Core™ Processors and Intel Atom® Processors x7000E Series, they will not impact the availability of Intel® TCC Tools release 2022.2 or its availability on platforms launched prior to 2023.
Intel® TCC Tools was designed as a collection of APIs and libraries to simplify optimizations of real-time performance on Intel platforms by creating custom real-time tuning configurations to apply to systems. Extensive customer input and ongoing Intel research has shown that much of the functionality DSO and SWSRAM were designed to offer, can be delivered by other existing mechanisms when used in real-world deterministic applications. The majority of customers leverage Intel® TCC either via the functionality delivered out-of-box on our real-time capable platforms or by enabling TCC Mode in UEFI BIOS or Slim Bootloader.
Even though it is expected that the changes to Intel® TCC tools will have little to no impact to our customers and ISV partners, we are providing this communication to ensure clear messaging to all stakeholders, internal and external. If you have questions or have a customer with specific needs that may not be apparent on how to meet, please contact your technical support team for more details.
- Customer support
Contact your Intel representative or submit an issue to Intel Premier Support.
Note
Intel® TCC Tools is independent of the Intel® ECI release lifecycle. Current version of ECI supports Intel® Time Coordinated Computing Tools 2022.2 .
Intel® TCC is officially supported on 12th and 11th Gen Intel® Core™ processors, as well as developer preview on Intel Atom® x6000E Series processors (list of supported processors).
ECI Linux* Intel LTS kernel provides built-in RCTM (CONFIG_X86_TCC_PTCM) drivers and UEFI/BIOS TCC Mode enabled Firmware are mandatory requirements as documented in Real-Time Tuning Guide 11th Generation Intel® Core™ Processors, and Real-Time Tuning Guide Atom® x6000E Series .
Setup the ECI APT repository and check if Intel® TCC Tools 2022.2 Deb packages is listed:
$ apt list | grep -e tcc-tools -e libtcc -e rtcm
The following is the expected output for Debian 11 (Bullseye) ECI APT repository.
libtcc-dbgsym/unknown 2022.2.0-bullseye-3.e8cd3f2117 amd64
libtcc-dev/unknown 2022.2.0-bullseye-3.e8cd3f2117 amd64
libtcc/unknown 2022.2.0-bullseye-3.e8cd3f2117 amd64
rtcm-efi/unknown 4.02-bullseye-2.d08fdc155c amd64
tcc-tools-common-dbgsym/unknown 2022.2.0-bullseye-3.e8cd3f2117 amd64
tcc-tools-common-dev/unknown 2022.2.0-bullseye-3.e8cd3f2117 amd64
tcc-tools-common/unknown 2022.2.0-bullseye-3.e8cd3f2117 amd64
tcc-tools-grub/unknown 1.0 amd64
tcc-tools-measurements-dbgsym/unknown 2022.2.0-bullseye-3.e8cd3f2117 amd64
tcc-tools-measurements-dev/unknown 2022.2.0-bullseye-3.e8cd3f2117 amd64
tcc-tools-measurements/unknown 2022.2.0-bullseye-3.e8cd3f2117 amd64
tcc-tools-ssram-dev-dbgsym/unknown 2022.2.0-bullseye-3.e8cd3f2117 amd64
tcc-tools-ssram-dev/unknown 2022.2.0-bullseye-3.e8cd3f2117 amd64
tcc-tools-timesync-dbgsym/unknown 2022.2.0-bullseye-3.e8cd3f2117 amd64
tcc-tools-timesync-dev/unknown 2022.2.0-bullseye-3.e8cd3f2117 amd64
tcc-tools-timesync/unknown 2022.2.0-bullseye-3.e8cd3f2117 amd64
Follow the steps in the Intel TCC Tools Get Started Guide.
Note: The TCC Tools Get Started Guide provides the steps to build and install a Yocto image. You have already completed these steps in ECI, hence skip the following steps: Step 1: Build Yocto Project-Based Image and Step 5: Install on Target.
Intel TCC Tools - Resources¶
For help and support, refer to the following:
Developer Guide (If you do not have access to the Developer Guide, contact your Intel representative for assistance with accessing Intel TCC Tools).
Intel TCC Tools - Setup UEFI/BIOS Firmware¶
The following section is applicable to:

Verify that the target system (where Intel TCC Tools will run) contains a compatible UEFI/BIOS Firmware. Refer to the following table below for supported BIOS versions:
Commercial Off-the-shelf Product Name Intel Processor Model Commercial Firmware Release
(IFWI Version Kit)Firmware Enabled with Cache Reservation Library (CRL) Intel TCC Tools Compatibility Intel® platform IFWI Reference CRL version for 11th Generation Intel® Core (IFWI Firmware Kit 647009) EHLSFWI1.R00.3432.A03.2110250557
(Current IFWI version: v3441.01)V5.11 2022.2 ASRock iEP-5000G Atom x6425RE L1.42 V5.11 2022.2 Intel® platform IFWI Reference CRL version for Atom x6000 series (IFWI Firmware Kit 647009) TGLIFUI1.R00.4391.A01.2110081311
(Current IFWI version: v4415_01)V5.07 2022.2 Vecow SPC-7100GRE 11th Gen i7-1185GRE E5000XXU3FRT103 V2.0 2021.x legacy Intel® platform IFWI Reference CRL version for 12th Generation Intel® Core (IFWI Firmware Kit 647009) ADLSFWI1.R00.3125.B00.2203201519 V5.52 2022.2 IEI TANK-XM811 12th Gen i7-12700E 5.25 V5.11 2022.2 ASrock iEP-9010E 12th Gen i7-12700E L0.19A V5.5 2022.2 Important
If your ODM UEFI BIOS is not compatible, contact your Intel representative for assistance or create a ticket in Premier Support. To create a ticket, log in with Intel® account, create a new Intel Edge Software Recipes Case under the Category Software/Driver/OS and the Subcategory Industrial Edge Control Software.
Boot the target system and access the BIOS (press the delete or F2 keys while booting to open the BIOS menu).
Configure Software-SRAM (SSRAM) and Data Streams Optimizer (DSO) from the target system UEFI/BIOS menu according to the table listed in the tab corresponding to your system.
Note: Click the tab corresponding to your system.
Setting Name Option Setting Menu Intel(R) TCC Authentication Disabled Intel Advanced Menu ⟶ Intel Time Coordinated Computing Software-SRAM Enabled Intel Advanced Menu ⟶ Intel Time Coordinated Computing Data Streams Optimizer Enabled Intel Advanced Menu ⟶ Intel Time Coordinated Computing Intel (VMX) Virtualization Enabled Intel Advanced Menu ⟶ CPU Configuration Setting Name Option Setting Menu Intel(R) TCC Authentication Disabled Intel Advanced Menu ⟶ Intel Time Coordinated Computing Intel (VMX) Virtualization Enabled Intel Advanced Menu ⟶ CPU Configuration Setting Name Option Setting Menu Intel(R) TCC Authentication Disabled Intel Advanced Menu ⟶ Intel Time Coordinated Computing Intel (VMX) Virtualization Enabled Intel Advanced Menu ⟶ CPU Configuration Setting Name Option Setting Menu Intel(R) TCC Authentication Disabled Intel Advanced Menu ⟶ Intel Time Coordinated Computing Software SRAM Enabled Intel Advanced Menu ⟶ Intel Time Coordinated Computing Data Streams Optimizer Enabled Intel Advanced Menu ⟶ Intel Time Coordinated Computing Intel (VMX) Virtualization Enabled Intel Advanced Menu ⟶ CPU Configuration Configure the Time-Aware GPIO (TGPIO) from the target system UEFI/BIOS menu according to the table listed in the tab corresponding to your system.
Note: Click the tab corresponding to your system.
Setting Name Option Setting Menu Enabled Timed GPIO0 Enabled Intel Advanced Menu ⟶ PCH IO Configuration Enabled Timed GPIO1 Enabled Intel Advanced Menu ⟶ PCH IO Configuration Intel (VMX) Virtualization Enabled Intel Advanced Menu ⟶ CPU Configuration Setting Name Option Setting Menu Force Unlock on all GPIO Pads Enabled Intel Advanced Menu ⟶ PCH IO Configuration ⟶ Security Configuration SPI2 Controller Disabled Intel Advanced Menu ⟶ PCH IO Configuration ⟶ SerialIo Configuration GPIO/TGPIO 0 Host owned with pin muxed Intel Advanced Menu ⟶ PCH IO Configuration ⟶ PSE configuration GPIO/TGPIO 0 MUX Selection/td> MID Intel Advanced Menu ⟶ PCH IO Configuration ⟶ PSE configuration GPIO/TGPIO 0 Pin Selection Check pins 28 and 27 Intel Advanced Menu ⟶ PCH IO Configuration ⟶ PSE configuration Intel TCC Tools - Enable Linux Software-SRAM (SSRAM)¶
The following section is applicable to:

Attention
Intel® TCC 2022.2 does not coexist with Intel® Resource Director Technology (Intel® RDT). Intel® TCC 2022.2 recommends to disable Cache Allocation Technology (CAT) using kernel command-line
rdt=!l2cat,!l3cat.The methods to enable Intel TCC Tools vary depending on whether the Linux OS environment is bare-metal or virtualized using the ACRN Hypervisor.
If the Linux OS environment you are using is a virtual machine (VM) running on the ACRN Hypervisor, select the Intel TCC Enabled Baremetal Linux OS tab. Otherwise, select the Intel TCC Enabled ACRN Service and User Linux OS tab.
Note: If you are using with the ACRN Hypervisor, install Intel TCC Tools on both the ACRN Service VM and the User VM.
For further information, refer to the Intel TCC Tools Developer Guide.
After completing this section, you will have enabled the TCC Software-SRAM buffer, updated the TCC cache BIOS sub-region via a firmware update mechanism, and verified the system configuration.
Step 1: Complete the Prerequisites
Make sure that the Intel TCC Tools - Setup UEFI/BIOS Firmware section has been completed.
Step 2: Configure Software-SRAM from Linux OS
Install Intel® Linux RT kernel Deb packages with Linux built-in kernel PTCM driver (for example,
CONFIG_X86_TCC_PTCM) on the target machine:$ sudo apt install linux-intel-rt
Install TCC RTCM bootloader EFI application and TCC GRUB custom entries on the target machine:
$ sudo apt install rtcm-efi tcc-tools-grub
Reading package lists... Done Building dependency tree... Done Reading state information... Done The following additional packages will be installed: efibootmgr libpopt0 The following NEW packages will be installed: efibootmgr libpopt0 rtcm-efi tcc-tools-grub 0 upgraded, 4 newly installed, 0 to remove and 9 not upgraded. Need to get 118 kB of archives. After this operation, 488 kB of additional disk space will be used. Do you want to continue? [Y/n] y Get:1 http://lava.lavalab/mirrors/debian bullseye/main amd64 libpopt0 amd64 1.18-2 [49.6 kB] Get:2 http://lava.lavalab/mirrors/debian bullseye/main amd64 efibootmgr amd64 17-1 [31.2 kB] Get:3 http://lava.lavalab/tftp/u/razvan/latest-bullseye/eci-bullseye isar/main amd64 rtcm-efi amd64 4.02-bullseye-2.d08fdc155c [35.3 kB] Get:4 http://lava.lavalab/tftp/u/razvan/latest-bullseye/eci-bullseye isar/main amd64 tcc-tools-grub amd64 1.0 [1928 B] Fetched 118 kB in 0s (286 kB/s) debconf: delaying package configuration, since apt-utils is not installed ... Selecting previously unselected package rtcm-efi. Preparing to unpack .../rtcm-efi_4.02-bullseye-2.d08fdc155c_amd64.deb ... Unpacking rtcm-efi (4.02-bullseye-2.d08fdc155c) ... Selecting previously unselected package tcc-tools-grub. Preparing to unpack .../tcc-tools-grub_1.0_amd64.deb ... Unpacking tcc-tools-grub (1.0) ... Setting up tcc-tools-grub (1.0) ... Generating grub configuration file ... Found linux image: /boot/vmlinuz-5.10.115-rt67-intel-ese-standard-lts-rt+ Found initrd image: /boot/initrd.img-5.10.115-rt67-intel-ese-standard-lts-rt+ Found linux image: /boot/vmlinuz-5.10.115-rt67-intel-ese-standard-lts-rt+ Found initrd image: /boot/initrd.img-5.10.115-rt67-intel-ese-standard-lts-rt+ Adding boot menu entry for EFI firmware configuration done ... Setting up rtcm-efi (4.02-bullseye-2.d08fdc155c) ... CONFIG_X86_TCC_PTCM found Generating grub configuration file ... Found linux image: /boot/vmlinuz-5.10.115-rt67-intel-ese-standard-lts-rt+ Found initrd image: /boot/initrd.img-5.10.115-rt67-intel-ese-standard-lts-rt+ Found linux image: /boot/vmlinuz-5.10.115-rt67-intel-ese-standard-lts-rt+ Found initrd image: /boot/initrd.img-5.10.115-rt67-intel-ese-standard-lts-rt+ Adding boot menu entry for EFI firmware configuration done
Install Intel® TCC tool
ssramDeb package with TCC setup scripts on the Linux target machine:$ sudo apt install eci-realtime-tcc
The following setup will activate a pre-defined configuration for the Software-SRAM. This includes:
Enabling the TCC Driver to be auto-loaded
Creating BIOS capsules with the updated cache configuration, which will be deployed to the BIOS sub-regions when the system is re-booted.
Configure the Software-SRAM buffer. From the following table, run the command corresponding to your target system:
Target System
Command
12th and 11th Gen Intel® Core™ Processors
$ sudo /usr/share/tcc_tools/scripts/setup_ssram/tcc_setup_ssram.sh enable
Intel® Atom™ x6000 Processors
$ sudo /usr/share/tcc_tools/scripts/setup_ssram/tcc_setup_ssram.sh enable
Vecow* SPC-7100GRE (2021.x-legacy)
$ sudo /usr/share/tcc_tools/scripts/setup_ssram_v1/tcc_setup_ssram.sh enable -c core_i7
ASRock* iEP-9010E
$ sudo /usr/share/tcc_tools/scripts/setup_ssram_v1/tcc_setup_ssram.sh enable
iEi* TANK-XM811
$ $ sudo /usr/share/tcc_tools/scripts/setup_ssram/tcc_setup_ssram.sh enable
The target system will reboot twice during the BIOS update process. Do not interrupt this process. On the first reboot, the BIOS will locate and load the capsules, as shown in the figure below:
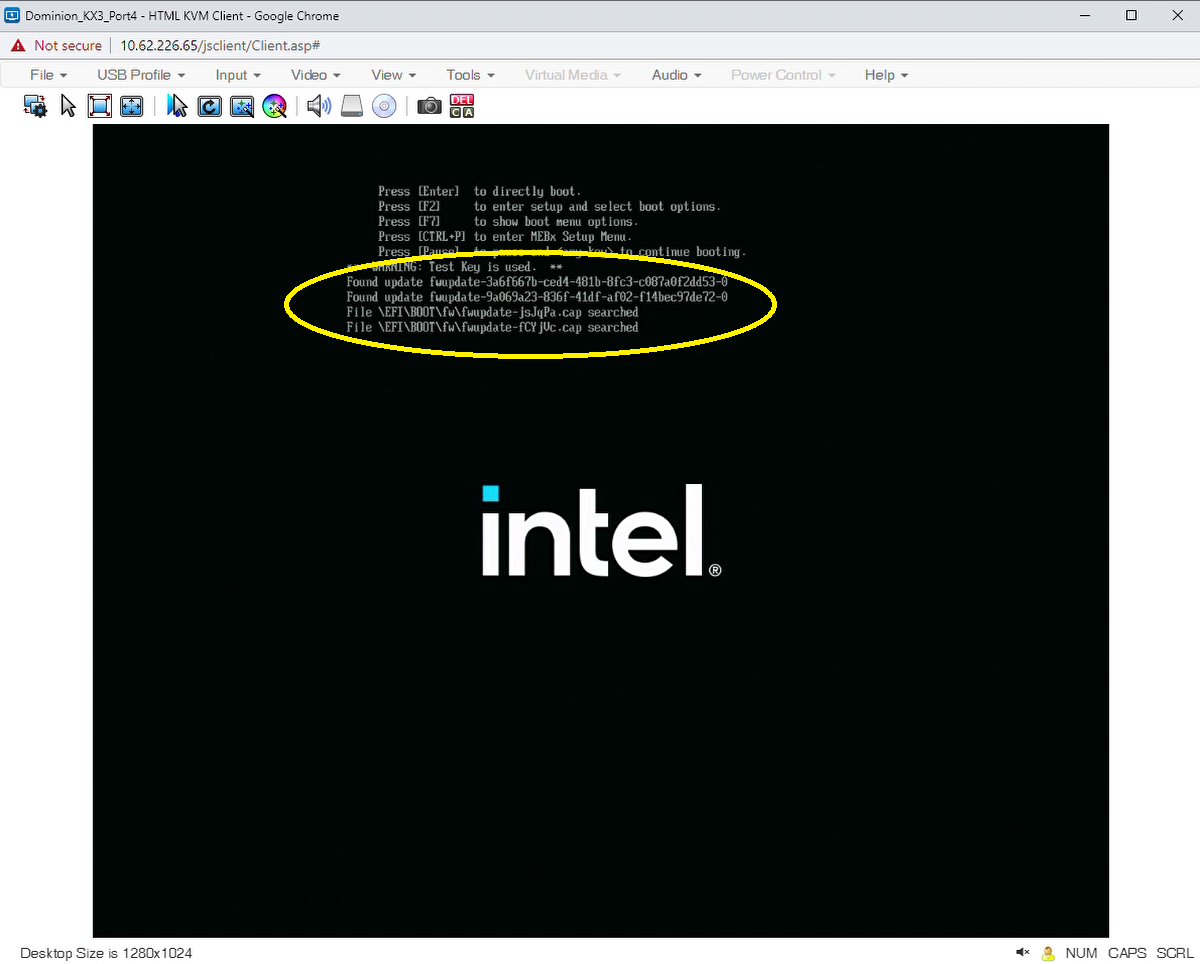
On the second reboot, the BIOS will apply the capsules. Typically a progress bar appears during this process, as shown in the figure below:
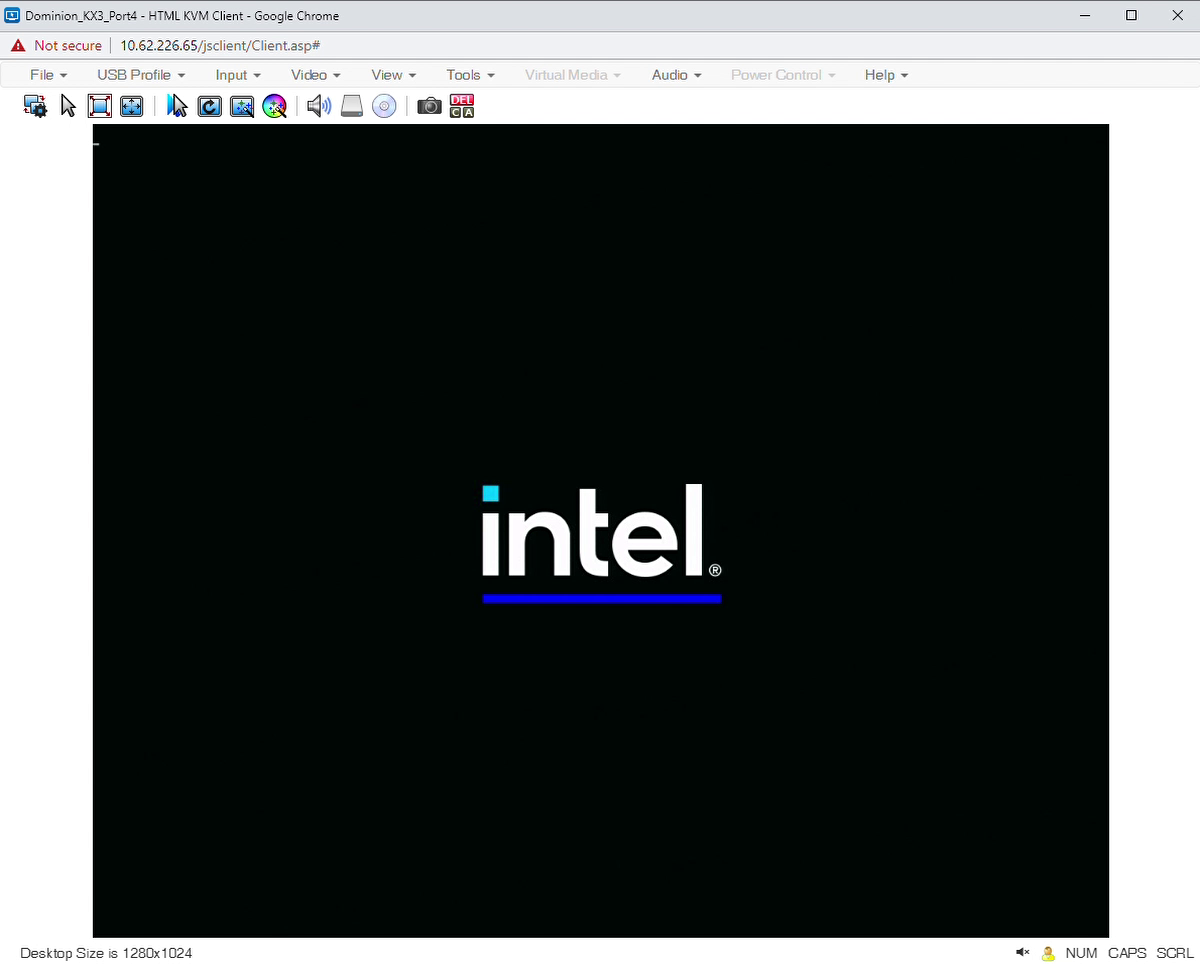
After the target system has fully booted, login again. Verify the system configuration. From the following table, run the command corresponding to your target system:
Target System
Command
12th and 11th Gen Intel® Core™ Processors
To verify:
$ sudo /usr/share/tcc_tools/scripts/setup_ssram/tcc_setup_ssram.sh enable --verify
To disable Intel TCC Tools:
$ /usr/share/tcc_tools/scripts/setup_ssram/tcc_setup_ssram.sh disable
Intel® Atom™ x6000 Processors
To verify:
$ sudo /usr/share/tcc_tools/scripts/setup_ssram/tcc_setup_ssram.sh enable --verify
To disable Intel TCC Tools:
$ /usr/share/tcc_tools/scripts/setup_ssram/tcc_setup_ssram.sh disable
Vecow* SPC-7100GRE (2021.x-legacy)
To verify:
$ sudo /usr/share/tcc_tools/scripts/setup_ssram_v1/tcc_setup_ssram.sh enable -c core_i7 --verify
To disable Intel TCC Tools:
$ /usr/share/tcc_tools/scripts/setup_ssram_v1/tcc_setup_ssram.sh disable
ASRock* iEP-9010E
To verify:
$ sudo /usr/share/tcc_tools/scripts/setup_ssram_v1/tcc_setup_ssram.sh enable -c core_i7--verify
To disable Intel TCC Tools:
$ /usr/share/tcc_tools/scripts/setup_ssram_v1/tcc_setup_ssram.sh disable -c core_i7
iEi* TANK-XM811
To verify:
$ sudo /usr/share/tcc_tools/scripts/setup_ssram/tcc_setup_ssram.sh enable -c core_i7 --verify
To disable Intel TCC Tools:
$ /usr/share/tcc_tools/scripts/setup_ssram/tcc_setup_ssram.sh disable -c core_i7
The script verifies whether the TCC Driver is loaded and if the RTCT table, found at
/sys/firmware/acpi/tables/PTCT, complies with the pre-defined Software-SRAM configuration. If everything is correct, the script will output the following:verify [ENABLED ] Driver [ENABLED ] Driver auto-load [VALID ] Cache configuration (from RTCT) SYSTEM CONFIGURATION IS CORRECT
Decode the RTCT table and verify that it contains an active Software-SRAM configuration by performing the following command:
$ sudo /usr/share/tcc_tools/tools/tcc_cache_info_read.py | grep -C 8 SRAM
If the pre-defined Software-SRAM configuration is active, this command should report three records with Software-SRAM buffers (the values will be different depending on CPU SKU):
{ "Level": 2, "Cache_ID": 2, "Base": 1074266112, "Size": 262144, "Shared": 0, "Type": "common.rtct.v2.rtct.SoftwareSRAM" }, { "Level": 2, "Cache_ID": 3, "Base": 1074528256, "Size": 262144, "Shared": 0, "Type": "common.rtct.v2.rtct.SoftwareSRAM" }, { "Level": 3, "Cache_ID": 0, "Base": 1074266112, "Size": 1048576, "Shared": 0, "Type": "common.rtct.v2.rtct.SoftwareSRAM" },
Reboot and ECI GRUB entry.
Run the
tcc_cache_allocation_sampleto verify whether Intel TCC is correctly working.Once the driver is enabled, perform the following commands to run the Intel TCC example:
$ sudo export TCC_LOG_LEVEL=INFO $ sudo tcc_cache_allocation_sample --collect --latency 100 --stress --cpuid 1
Note: You may need to increase the
--latencyparameter to better match the platform being tested.The expected output should be similar to the following:
Running with arguments: latency = 100 ns, stress = internal, iterations = 100, collector = libtcc_collector.so, mask interrupts = true : print_regions_table | Available regions: print_regions_table | Id Cache level Latency, ns Affinity mask Entire region size, b Allocation size from tcc.config, b print_regions_table | 4294967295 TCC_MEM_DRAM 114 11000000 Regular RAM Regular RAM print_regions_table | 2 TCC_MEM_L3 49 11000000 524288 262144 print_regions_table | 0 TCC_MEM_L2 6 10000000 262144 98304 print_regions_table | 1 TCC_MEM_L2 6 01000000 262144 98304 Allocating memory according to the latency requirements allocators_manager_get_next | Searching for memory to satisfy requirements: latency=50 ns, affinity=01000000 allocators_manager_get_next | Found suitable allocator for request: region #1 (TCC_MEM_L3) region_allocator_malloc | Calling region malloc with: size=97280 Running workload. This may take a while, depending on sleep and iteration values Deallocating memory *** Statistics for workload **************************** Minimum total latency: 21898 CPU cycles (7811 ns) Maximum total latency: 24051 CPU cycles (8579 ns) Average total latency: 22703 CPU cycles (8098 ns) Minimum latency per buffer access: 43 CPU cycles (15 ns) Maximum latency per buffer access: 47 CPU cycles (16 ns) Average latency per buffer access: 44 CPU cycles (15 ns) ********************************************************
Attention
Time-Aware GPIO is not validated with ACRN.
Attention
TCC cache-configurator is not supported on Vecow SPC-7100 with ACRN.
Step 1: Install the ACRN Hypervisor
If not already completed, install the ACRN Hypervisor. Note: ACRN built using Legacy Yocto is not supported!
Step 2: Complete the Prerequisites
Make sure that the Intel TCC Tools - Setup UEFI/BIOS Firmware section has been completed.
Note: For now, only install TCC Tools onto the ACRN Service VM. The later steps will address the User VM.
Step 3: Configure Software-SRAM from ACRN Service OS
Install Intel® Linux RT kernel Deb packages with Linux built-in kernel PTCM driver (for example,
CONFIG_X86_TCC_PTCM) on the ACRN Service OS:$ sudo apt install linux-intel-acrn-sos
Install TCC RTCM bootloader EFI application and TCC GRUB custom entries on the ACRN Service OS:
$ sudo apt install rtcm-efi tcc-tools-grub
Reading package lists... Done Building dependency tree... Done Reading state information... Done The following additional packages will be installed: efibootmgr libpopt0 The following NEW packages will be installed: efibootmgr libpopt0 rtcm-efi tcc-tools-grub 0 upgraded, 4 newly installed, 0 to remove and 9 not upgraded. Need to get 118 kB of archives. After this operation, 488 kB of additional disk space will be used. Do you want to continue? [Y/n] y Get:1 http://lava.lavalab/mirrors/debian bullseye/main amd64 libpopt0 amd64 1.18-2 [49.6 kB] Get:2 http://lava.lavalab/mirrors/debian bullseye/main amd64 efibootmgr amd64 17-1 [31.2 kB] Get:3 http://lava.lavalab/tftp/u/razvan/latest-bullseye/eci-bullseye isar/main amd64 rtcm-efi amd64 4.02-bullseye-2.d08fdc155c [35.3 kB] Get:4 http://lava.lavalab/tftp/u/razvan/latest-bullseye/eci-bullseye isar/main amd64 tcc-tools-grub amd64 1.0 [1928 B] Fetched 118 kB in 0s (286 kB/s) debconf: delaying package configuration, since apt-utils is not installed ... Selecting previously unselected package rtcm-efi. Preparing to unpack .../rtcm-efi_4.02-bullseye-2.d08fdc155c_amd64.deb ... Unpacking rtcm-efi (4.02-bullseye-2.d08fdc155c) ... Selecting previously unselected package tcc-tools-grub. Preparing to unpack .../tcc-tools-grub_1.0_amd64.deb ... Unpacking tcc-tools-grub (1.0) ... Setting up tcc-tools-grub (1.0) ... Generating grub configuration file ... Found linux image: /boot/vmlinuz-5.10.115-acrn-sos-intel-ese-standard-lts Found initrd image: /boot/initrd.img-5.10.115-acrn-sos-intel-ese-standard-lts Adding boot menu entry for EFI firmware configuration done ... Setting up rtcm-efi (4.02-bullseye-2.d08fdc155c) ... CONFIG_X86_TCC_PTCM found Generating grub configuration file ... Found linux image: /boot/vmlinuz-5.10.115-acrn-sos-intel-ese-standard-lts Found initrd image: /boot/initrd.img-5.10.115-acrn-sos-intel-ese-standard-lts Adding boot menu entry for EFI firmware configuration done
Install Intel® TCC tool
commonDeb package with TCC setup scripts on the Linux ACRN Service OS:$ sudo apt install tcc-tools-common
The following setup will activate a pre-defined configuration for the Software-SRAM. This includes:
Enabling the TCC Driver to be auto-loaded
Creating BIOS capsules with the updated cache configuration, which will be deployed to the BIOS sub-regions when the system is re-booted.
Reboot the target system. From the GRUB boot option menu, select ECI Debian or ECI Ubuntu without ACRN and then press Enter.
$ sudo reboot
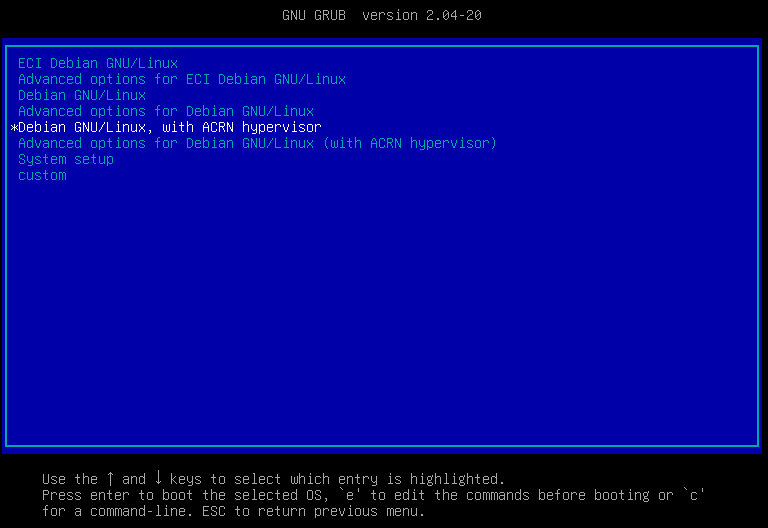
Login to the target system and configure the Software-SRAM buffer. From the following table, run the command corresponding to your target system:
Target System
Command
12th and 11th Gen Intel® Core™ Processors
$ sudo /usr/share/tcc_tools/scripts/setup_ssram/tcc_setup_ssram.sh enable
Intel® Atom™ x6000 Processors
$ sudo /usr/share/tcc_tools/scripts/setup_ssram/tcc_setup_ssram.sh enable
Vecow* SPC-7100GRE (2021.x-legacy)
$ sudo /usr/share/tcc_tools/scripts/setup_ssram_v1/tcc_setup_ssram.sh enable --cpu core_i7
Note:
setup_ssram_v1is a fallback option for Vecow* SPC-7100 (Tiger Lake UP3) with UEFI IA firmware legacy RTCDv1 with IFWI version E5000XXU3F00105-BPCIe and E5000X7U3FRT103. Contact your ODM representative for assistance.
The target system will reboot twice during the BIOS update process. Do not interrupt this process. On the first reboot, the BIOS will locate and load the capsules, as shown in the figure below:

On the second reboot, the BIOS will apply the capsules. Typically a progress bar appears during this process, as shown in the figure below:

Step 4: Verify Target System Setup
After the target system has rebooted and displays the GRUB boot option menu, select ECI Debian or ECI Ubuntu without ACRN and then press Enter.

After the target system has fully booted, login again. Verify the system configuration. From the following table, run the command corresponding to your target system:
Target System
Command
12th and 11th Gen Intel® Core™ Processors
$ sudo /usr/share/tcc_tools/scripts/setup_ssram/tcc_setup_ssram.sh enable --verify
Intel® Atom™ x6000 Processors
$ sudo /usr/share/tcc_tools/scripts/setup_ssram/tcc_setup_ssram.sh enable --verify
Vecow* SPC-7100GRE (2021.x-legacy)
$ sudo /usr/share/tcc_tools/scripts/setup_ssram_v1/tcc_setup_ssram.sh enable --verify --cpu core_i7
Note:
setup_ssram_v1is a fallback option for Vecow* SPC-7100 (Tiger Lake UP3) with UEFI IA firmware legacy RTCDv1 with IFWI version E5000XXU3F00105-BPCIe and E5000X7U3FRT103. Contact your ODM representative for assistance.The script verifies whether the TCC Driver is loaded and if the RTCT table, found at
/sys/firmware/acpi/tables/PTCT, complies with the pre-defined Software-SRAM configuration. If everything is correct, the script will output the following:verify [ENABLED ] Driver [ENABLED ] Driver auto-load [VALID ] Cache configuration (from RTCT) SYSTEM CONFIGURATION IS CORRECT
Decode the RTCT table and verify that it contains an active Software-SRAM configuration by performing the following command:
$ sudo tcc_cache_info_read | grep -C 8 SoftwareSRAM
If the pre-defined Software-SRAM configuration is active, this command should report three records with Software-SRAM buffers:
{ "Level": 2, "Cache_ID": 2, "Base": 1074266112, "Size": 262144, "Shared": 0, "Type": "common.rtct.v2.rtct.SoftwareSRAM" }, { "Level": 2, "Cache_ID": 3, "Base": 1074528256, "Size": 262144, "Shared": 0, "Type": "common.rtct.v2.rtct.SoftwareSRAM" }, { "Level": 3, "Cache_ID": 0, "Base": 1074266112, "Size": 1048576, "Shared": 0, "Type": "common.rtct.v2.rtct.SoftwareSRAM" },
Step 5: Change Boot Order
You can optionally change the boot order of the system. This will reduce the need to enter BIOS to boot from a specific device. Using the following example, you can control the boot order of your system.
After verifying whether the Software-SRAM capsule has been applied correctly, you can remove the
RTCMboot option as it is not required anymore. Run the following command:#Replace '<bootnum>' with the number corresponding to "RTCM". Example has been provided below. $ sudo efibootmgr -b <bootnum> -B
root@eci-intel-0faa:~# efibootmgr BootCurrent: 0006 Timeout: 5 seconds BootOrder: 0006,0005,0004,0001,0002,0000,0003 Boot0000* Enter Setup Boot0001* Internal UEFI Shell Boot0002* Boot Device List Boot0003* UEFI SanDisk Extreme 4C530001091014102431 Boot0004* UEFI Samsung SSD 970 EVO Plus 500GB S58SNJ0N610041M 1 Boot0005* ECI Boot0006* RTCM root@eci-intel-0faa:~# efibootmgr -b 0006 -B BootCurrent: 0006 Timeout: 5 seconds BootOrder: 0005,0004,0001,0002,0000,0003 Boot0000* Enter Setup Boot0001* Internal UEFI Shell Boot0002* Boot Device List Boot0003* UEFI SanDisk Extreme 4C530001091014102431 Boot0004* UEFI Samsung SSD 970 EVO Plus 500GB S58SNJ0N610041M 1 Boot0005* ECI
Step 6: Launch the Linux Real-time ACRN User VM
Boot into the ACRN boot option and launch a real-time User OS VM.
After validating the system, reboot the system. When the GRUB menu appears, let the system boot normally. The ACRN option will be selected, by default.
$ sudo reboot
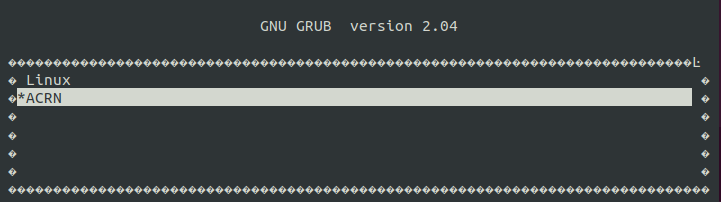
Login to the ACRN Service VM and verify that a VM image exists at
/var/lib/machines/images/uos_vm1.img. If a VM image does not exist, copy a VM image to/var/lib/machines/images/uos_vm1.img.Tip
The ECI core-bullseye and core-jammy images can be used as-is with ACRN. To use these images as VMs, first build the image(s) by completing one of the following sections: core-bullseye, core-jammy. After the build has completed, there will a
*.wic.imgfile available at/eci-release/build/eci-core-<distribution>/tmp/deploy/images/x86-64-efi/eci-image-<distribution>-minimal-eci-<distribution>-x86-64-efi.wic.img(Replace<distribution>withbullseyeorjammy). Use this file as the VM image.Launch the real-time VM:
$ /var/lib/machines/scripts/launch-rtvm.sh
Step 7: Install Intel TCC Tools on the Linux ACRN User VM
Install the Intel TCC Tools common and ssram Deb package on the User OS.
The boot up of the real-time VM will take few minutes and will eventually present a login console. Login to the VM, then run the following command to install the Intel TCC Tools:
$ sudo apt install tcc-tools-ssram-dev
Step 8: Enable Intel TCC Driver on the Linux ACRN User VM
Enable Intel TCC Driver. This will allow the VM to read the cache configuration.
$ sudo /usr/share/tcc_tools/scripts/setup_ssram/control_tcc_driver.sh enable
Step 9: Verify Intel TCC on the ACRN User VM
Run the
tcc_cache_allocation_sampleto verify whether Intel TCC is correctly working on the VM.Once the driver is enabled, perform the following commands to run the Intel TCC example:
$ sudo export TCC_LOG_LEVEL=INFO $ sudo tcc_cache_allocation_sample --collect --latency 50 --stress --cpuid 1
The expected output should be similar to the following:
Running with arguments: latency = 50 ns, stress = internal, iterations = 100, collector = libtcc_collector.so, mask interrupts = true : print_regions_table | Available regions: print_regions_table | Id Cache level Latency, ns Affinity mask Entire region size, b Allocation size from tcc.config, b print_regions_table | 4294967295 TCC_MEM_DRAM 114 11000000 Regular RAM Regular RAM print_regions_table | 2 TCC_MEM_L3 49 11000000 524288 262144 print_regions_table | 0 TCC_MEM_L2 6 10000000 262144 98304 print_regions_table | 1 TCC_MEM_L2 6 01000000 262144 98304 Allocating memory according to the latency requirements allocators_manager_get_next | Searching for memory to satisfy requirements: latency=50 ns, affinity=01000000 allocators_manager_get_next | Found suitable allocator for request: region #1 (TCC_MEM_L3) region_allocator_malloc | Calling region malloc with: size=97280 Running workload. This may take a while, depending on sleep and iteration values Deallocating memory *** Statistics for workload **************************** Minimum total latency: 21898 CPU cycles (7811 ns) Maximum total latency: 24051 CPU cycles (8579 ns) Average total latency: 22703 CPU cycles (8098 ns) Minimum latency per buffer access: 43 CPU cycles (15 ns) Maximum latency per buffer access: 47 CPU cycles (16 ns) Average latency per buffer access: 44 CPU cycles (15 ns) ********************************************************
Intel TCC Tools - Cache Configurator¶
Attention
Intel® TCC 2022.2 does not coexist well with Intel® Resource Director Technology (Intel® RDT). Intel® TCC 2022.2 recommends that you disable Cache Allocation Technology (CAT) using kernel command line
rdt=!l2cat,!l3cat.The pre-configured BIOS capsules with the Software-SRAM configuration (set up in the previous sections) was deployed into the BIOS sub-regions as described in the Intel TCC Get Started Guide (Step 7 - Complete Target Setup of Software SRAM).
The pre-defined Software-SRAM configuration consists of three buffers:
One buffer located in L3 cache guaranteeing a maximum latency of 49 ns.
Two buffers located in L2 cache and guaranteeing a maximum latency of 6 ns.
While this pre-defined Software-SRAM configuration represents only a sample configuration, you can use the TCC Cache Configurator to create your own Software-SRAM configurations and deploy those onto the target board.
For more information on the working of the TCC Cache Configurator, refer to Cache Configurator.
The following steps, which provide details on how to use the cache configurator, correspond to Launch the Cache Configurator of the Intel® TCC Tools Developer Guide.
Install TCC
ssramtools and libraries on the target machine:$ sudo apt install tcc-tools-ssram-dev
On the target machine, enable the
tcc_bufferdriver (if it is not enabled already ):$ sudo /usr/share/tcc_tools/scripts/setup_ssram/control_tcc_driver.sh
Install TCC
hosttools and libraries on the host machine:$ sudo apt install tcc-host-tools
On the host machine, launch the TCC Cache Configurator.
Follow the steps in TCC Cache Configurator to set up cache configuration for the system.
Important
You will need to update the sample environment with the correct values for Intel® Core™ processors or Intel Atom® processors.
Intel TCC Tools - Enable Linux Time-Aware GPIO¶
Certain Intel® processors have a hardware feature called Time-Aware GPIO (TGPIO).
These processors have one or more TGPIO pins, which are clocked by invariant timekeeping hardware. You can program a specific timestamp to toggle a TGPIO pin, or capture the current timestamp when a pin is toggled. This is done by hardware, so the OS or other software does not affect the precision.
Recommended target processors are 11th Gen Intel® Core™ processors and Intel Atom® x6000E Series processors. See target processors for detailed recommendations.
For more specific usage of TGPIO, refer to Time-Aware GPIO (TGPIO) Samples.
Step 1: Complete the Prerequisites
Make sure that the Intel TCC Tools - Setup UEFI/BIOS Firmware section has been completed.
Note: For now, only install TCC Tools onto the ACRN Service VM. The later steps will address the User VM.
Step 2: Configure TGPIO driver for Linux Xenomai v3.2
Install Intel® Linux RT kernel Deb packages with Linux built-in kernel TGPIO driver (for example,
CONFIG_X86_TCC_PTCM) on the target machine:$ sudo apt install linux-intel-xenomai xenomai
Check whether the TGPIO driver is loaded successfully before toggling:
$ ls /dev/rtdm/pmc-tgpio or pse-tgpio
List all matching tests:
$ ./tgpiotest --list
The following tests should be listed:
#0 tgpio_oneshot_output TGPIO ONESHOT OUTPUT. device=<device-path>. pin=Specify the output pin index. Default: 0. channel=Specify the channel for the output pin. Default: 0. start=Specify the output delay in nanoseconds. Default: 1ms #1 tgpio_periodic_output TGPIO PERIODIC OUTPUT. device=<device-path>. pin=Specify the output pin index. Default: 0. channel=Specify the channel for the output pin. Default: 0. period=Specify the output period in nanoseconds. Default: 1ms #2 tgpio_input TGPIO INPUT. device=<device-path>. pin=Specify the input pin index. Default: 0. channel=Specify the channel for the output pin. Default: 0. mode=Specify interrupt or poll mode. 0:poll 1:interrupt. note: only pse-tgpio support interrupt mode. #3 tgpio_info Get TGPIO info. device=<device-path>.
Run test list:
$ ./tgpiotest --run=3 --verbose=4 device=/dev/rtdm/pmc-tgpio
The following tests should be completed:
tgpiotest.c:535, Available capabilities: Pins: 2 Input function - External timestamp channels: 2 Output function - Programmable periodic signals: 2 Precise system-device cross-timestamps: Supported tgpiotest.c:547, Available TGPIO pins: tgpiotest.c:548, Pin Name Index Used Function Channel tgpiotest.c:555, intel-pmc-tgpio-pin01 0 None 0 tgpiotest.c:555, intel-pmc-tgpio-pin02 1 None 1
For more information on test:
$ ./tgpiotest --help
A help message similar to the following should be printed:
based on Xenomai/cobalt v3.2 -- # () usage: tgpiotest <options>: --keep-going don\'t stop upon test error --list[=<id[,id...]>]] list [matching] tests --run[=<id[,id...]>]] run [portion of] the test list --exclude=<id[,id...]>] exclude test(s) from the run list --vm hint about running in a virtual environment --main-prio=<prio> main thread priority --print-buffer-size=<bytes> size of a print relay buffer (16k) --print-buffer-count=<num> number of print relay buffers (4) --print-sync-delay=<ms> max delay of output synchronization (100 ms) --cpu-affinity=<cpu[,cpu]...> set CPU affinity of threads --[no-]sanity disable/enable sanity checks --verbose[=level] set verbosity to desired level [=1] --silent, --quiet same as --verbose=0 --trace[=level] set tracing to desired level [=1] --version get version information --dump-config dump configuration settings --help display help
TGPIO I/O Test with Latmus¶
You can use latmus part for
xenomaiDeb package for input and output testing of TGPIO.Check if there is a TGPIO device:
$ ls /dev/rtdm/pmc-tgpio or pse-tgpio
Run the TGPIO input and output loop test.
Important
Activate the TGPIO pin. For more information, refer to Intel TCC Tools - Setup UEFI/BIOS Firmware. In the hardware platform used in this example, the TGPIO pins are pin 27 and pin 28.
$ latmus --pse-tgpio-out=pse-tgpio,18,1000000
Note: pin27 > pin=18 period: ns
$ latmus --pse-tgpio-in=pse-tgpio,17
Note: pin28 > pin=17
After connecting the two pins with wires, you will see the following output:
detected edge on channel 17 at 20:09:35.355067034 detected edge on channel 17 at 20:09:35.356066959 detected edge on channel 17 at 20:09:35.357067028 detected edge on channel 17 at 20:09:35.358067024 detected edge on channel 17 at 20:09:35.359067055 detected edge on channel 17 at 20:09:35.360066966 detected edge on channel 17 at 20:09:35.361067035 detected edge on channel 17 at 20:09:35.362067016 detected edge on channel 17 at 20:09:35.363067026 detected edge on channel 17 at 20:09:35.364067001
For more command arguments:
usage: latmus [options]: -m --measure measure latency on timer event [default] -t --tune tune the COBALT core timer -i --irq measure/tune interrupt latency -k --kernel measure/tune kernel scheduling latency -u --user measure/tune user scheduling latency [ if none of --irq, --kernel or --user is given, tune for all contexts ] -s --sirq measure in-band response time to synthetic irq -p --period=<us> sampling period -P --priority=<prio> responder thread priority [=90] -c --cpu=<n> pin responder thread to CPU [=current] -C --force-cpu=<n> similar to -c, accept non-isolated CPU -r --reset reset core timer gravity to factory default -b --background run in the background (daemon mode) -K --keep-going keep going on unexpected switch to in-band mode -A --max-abort=<us> abort if maximum latency exceeds threshold -T --timeout=<t>[dhms] stop measurement after <t> [d(ays)|h(ours)|m(inutes)|s(econds)] -v --verbose[=level] set verbosity level [=1] -q --quiet quiet mode (i.e. --verbose=0) -l --lines=<num> result lines per page, 0 = no pagination [=21] -H --histogram[=<nr>] set histogram size to <nr> cells [=200] -g --plot=<filename> dump histogram data to file (gnuplot format) -Z --oob-gpio=<host> measure COBALT response time to GPIO event via <host> -z --inband-gpio=<host> measure in-band response time to GPIO event via <host> -I --gpio-in=<spec> input GPIO line configuration with <spec> = gpiochip-devname,pin-number[,rising-edge|falling-edge] -O --gpio-out=<spec> output GPIO line configuration with <spec> = gpiochip-devname,pin-number -X --pse-tgpio-out=<spec> tgpio output mode with <spec> = devname,pin,period -x --pse-tgpio-in=<spec> tgpio input mode with <spec> = devname,pin
Intel TCC Tools - Sanity Checks¶
Run these sanity checks to make sure that the TCC tool is working.
Sanity Check 1: RT Checker¶
Intel TCC system hardware RT checker is a tool to make sure that the system is ‘RT READY’.
Run RT checker:
$ sudo /usr/bin/tcc_rt_checker
This will compare your current BIOS configuration with the best known configuration. If there is a mismatch, the message “NOT RT READY” will be displayed in red right next to it. You need to go into the BIOS and change the setting to the value provided by the output. After making all changes, rerun the RT checker executable to make sure system is ‘RT READY’.
Sanity Check 2: Verify TCC Drivers and Software-SRAM¶
After configuring TCC (see section Intel TCC Tools - Enable Linux Software-SRAM (SSRAM)), verify the system configuration. From the following table, run the command corresponding to your target system:
Target System
Command
12th and 11th Gen Intel® Core™ Processors
$ sudo /usr/share/tcc_tools/scripts/setup_ssram/tcc_setup_ssram.sh enable --verify
Intel® Atom™ x6000 Processors
$ sudo /usr/share/tcc_tools/scripts/setup_ssram/tcc_setup_ssram.sh enable --verify
Vecow* SPC-7100GRE (2021.x-legacy)
$ sudo /usr/share/tcc_tools/scripts/setup_ssram_v1/tcc_setup_ssram.sh enable --verify --cpu core_i7
Note:
setup_ssram_v1is a fallback option for Vecow* SPC-7100 (Tiger Lake UP3) with UEFI IA firmware legacy RTCDv1 with IFWI version E5000XXU3F00105-BPCIe and E5000X7U3FRT103. Contact your ODM representative for assistance.ASRock* iEP-9010E
$ sudo /usr/share/tcc_tools/scripts/setup_ssram/tcc_setup_ssram.sh enable --cpu core_i7 --verify
iEi* TANK-XM811
$ sudo /usr/share/tcc_tools/scripts/setup_ssram/tcc_setup_ssram.sh enable --cpu core_i7 --verify
The script verifies whether the TCC Driver is loaded and if the RTCT table, found at
/sys/firmware/acpi/tables/PTCT, complies with the pre-defined Software-SRAM configuration. If everything is correct, the script will output the following:verify [ENABLED ] Driver [ENABLED ] Driver auto-load [VALID ] Cache configuration (from RTCT) SYSTEM CONFIGURATION IS CORRECT
Troubleshooting¶
What is the Cache Reservation Library (CRL) version enabled by the OEM/ODM UEFI firmware?
Once the
rtcm-efiRTCM bootloader EFI application is installed and the system is rebooted usingtcc-tools-grubGRUB custom entries on the target machine, thelinux-image-intel-rtkernel image must load the Linux TCC buffer driver.$ sudo apt install linux-image-intel-rt rtcm-efi tcc-tools-grub $ reboot
The Cache Reservation Library (CRL) version available on your Intel® platform UEFI firmware integrated by OEM/ODM to Enable Intel® TCC, can be obtained as follow:
$ cat /proc/tcc_crlver
For version CRL v5.11 you would expect
000005115254434d 00000511
Any Intel® TCC Firmware sub-region configuration errors detected by Linux TCC buffer driver, can be obtained as follow:
$ cat /proc/tcc_errlog
errlog_addr @ 0000000040088000 errlog_size @ 000001e8 52524554 - Signature 00000001 - version 000001e8 - Subregion length 0000000a – Max DSO Error 0000000a – Max TCC configuration Error 00000000 – Number of Valid DSO Error 00000002 – Number of Valid Tcc Configuration Error ...
For more details see Intel® TCC BIOS Error Logging
Cache Configuration is INVALID
If the cache configuration is
INVALID, it means that the capsules have not been applied to the BIOS sub-regions. In most cases, this occurs if the system does not reboot appropriately and you have to run a power-off/power-on cycle. If the cache configuration is INVALID, repeat the steps listed in Intel TCC Tools - Enable Linux Software-SRAM (SSRAM).Only Driver is Disabled
If only the Driver is disabled, run the following command to enable it:
$ sudo /usr/share/tcc_tools/scripts/setup_ssram/control_tcc_driver.sh enable
If the above command does not work, run the following command to enable the driver (you need to rerun the command if the system is rebooted):
$ sudo modprobe tcc_buffer
+-----+------------------+------------------+------------------+--------------+ | Num | Checker name | Description | Note | Result | +-----+------------------+------------------+------------------+--------------+ | 1 | Hypervisor | Checks that the | Hypervisor is on | NA | | | detection | system was run | | | | | | from hypervisor | | | +-----+------------------+------------------+------------------+--------------+ | 2 | RTCM Checker | Checks that RTCM | Can't check | FAILED | | | | is enabled | current boot | | +-----+------------------+------------------+------------------+--------------+ | 3 | Real-time | Checks that | Real-time | NA | | | configuration | Real-time | configuration | | | | driver Checker | configuration | driver does not | | | | | driver exists | exist | | +-----+------------------+------------------+------------------+--------------+ | 4 | RT Kernel | Checks that RT | Current kernel | RT_READY | | | Checker | kernel is used | is RT | | +-----+------------------+------------------+------------------+--------------+ | 5 | GT CLOS Checker | Checks that GPU | Failed to check | FAILED | | | | doesn't overlap | GT CLOS due to | | | | | with dedicated | There is no | | | | | L3 CPU CLOS | corresponding | | | | | | SSRAM_WayMask | | | | | | entry for SSRAM | | | | | | SoftwareSRAM(Lev | | | | | | el=2, | | | | | | Cache_ID=0, | | | | | | Base=2130706432, | | | | | | Size=131072, | | | | | | Shared=0, Type=' | | | | | | common.rtct.v2.r | | | | | | tct.SoftwareSRAM | | | | | | ') | | +-----+------------------+------------------+------------------+--------------+ | 6 | Linux Kernel's | Checks that all | Cmdline | NON_RT_READY | | | command-line | kernel's | parameters that | | | | parameters | command-line par | are missing:art= | | | | Checker | ametersrequired | virtallow | | | | | for real-time | idle=poll rcupda | | | | | workload are set | te.rcu_cpu_stall | | | | | | _suppress=1 | | | | | | mce=off | | | | | | hpet=disable num | | | | | | a_balancing=disa | | | | | | ble | | | | | | igb.blacklist=no | | | | | | efi=runtime | | | | | | hugepages=1024 i | | | | | | 915.force_probe= | | | | | | * i915.enable_rc | | | | | | 6=0 | | | | | | i915.enable_dc=0 | | | | | | i915.disable_pow | | | | | | er_well=0 | | | | | | rcu_nocb_poll | | | | | | isolcpus=<list> | | | | | | rcu_nocbs=<list> | | +-----+------------------+------------------+------------------+--------------+ Real-time BIOS capabilities checkers: +-----+------------------+------------------+------------------+--------------+ | Num | Checker name | Description | Note | Result | +-----+------------------+------------------+------------------+--------------+ | 1 | Enhanced Intel | Checks that | Enhanced Intel | RT_READY | | | SpeedStep(R) | Enhanced Intel | SpeedStep(R) | | | | Technology | SpeedStep(R) | Technology is | | | | | Technology is | disabled | | | | | disabled | | | +-----+------------------+------------------+------------------+--------------+ | 2 | Intel(R) Speed | Check that | Intel(R) Speed | RT_READY | | | Shift Technology | Intel(R) Speed | Shift Technology | | | | | Shift Technology | is disabled | | | | | is disabled | | | +-----+------------------+------------------+------------------+--------------+ | 3 | Low Power S0 | Check that Low | Error in ACPI | FAILED | | | Idle Capability | Power S0 Idle is | table reading | | | | | disabled | | | +-----+------------------+------------------+------------------+--------------+ | 4 | CPU PCI Express | Check that CPU | | RT_READY | | | ASPM | PCI Express ASPM | | | | | | is disabled | | | +-----+------------------+------------------+------------------+--------------+ | 5 | Intel(R) Hyper- | Checks that | Intel(R) | RT_READY | | | Threading | Intel(R) | Hyperthreading | | | | Technology | Hyperthreading | Technology is | | | | | Technology is | disabled | | | | | disabled | | | +-----+------------------+------------------+------------------+--------------+ | 6 | Cache Allocation | Checks that | Cache Allocation | NON_RT_READY | | | Technology | Cache Allocation | Technology (CAT) | | | | | Technology is | is not supported | | | | | enabled | | | +-----+------------------+------------------+------------------+--------------+ | 7 | Cache Allocation | Checks that CAT | L3 CAT is | RT_READY | | | Technology | capabilities are | unsupported. L2 | | | | capabilities | enabled | CAT is | | | | | | unsupported. | | | | | | Memory Bandwidth | | | | | | Allocation (MBA) | | | | | | is unsupported. | | +-----+------------------+------------------+------------------+--------------+ | 8 | #AC Split Lock | When enabled, | #AC Split Lock | RT_READY | | | | generates an | is disabled | | | | | Alignment Check | | | | | | Exception when | | | | | | an application | | | | | | attempts to | | | | | | issue a split | | | | | | lock because a | | | | | | split lock | | | | | | increases | | | | | | latency. | | | +-----+------------------+------------------+------------------+--------------+
For more troubleshooting information, refer to: