Intel® Time Coordinated Computing Tools (Intel® TCC Tools)¶
Attention
For this Intel® ECI release, Intel® Time Coordinated Computing (Intel® TCC) is only supported on 11th Gen Intel® Core™ and Intel Atom® x6000E Series (as developer preview) processors! Other processors will be supported in future releases. Current version of ECI supports Intel® Time Coordinated Computing Tools 2021.3.
About Intel® TCC Tools¶
Intel processors are multi-purpose and can serve a wide range of use cases from data analysis in the cloud, to gaming PCs and traditional office laptops, to devices at the edge. Starting with Intel Atom® x6000E Series processors (code name: Elkhart Lake (EHL)) and 11th Gen Intel® Core™ processors (code name: Tiger Lake UP3 (TGL)), Intel is introducing a new set of features called Intel® Time Coordinated Computing (Intel® TCC) to augment the compute performance of its processors with ability to address the stringent temporal requirements of real-time applications. The ongoing industry transformation drives the demand for converged solutions capable of satisfying real-time requirements while staying generally power efficient and leaving sufficient performance for other concurrent tasks. The key value of Intel TCC is performance improvements for latency-sensitive applications when they are running alongside non-time-constrained applications on the same system.
While the Intel TCC features reside in the processor, their full potential is unlocked when the whole solution stack is optimized top-to-bottom. Intel offers a reference real-time software stack that abstracts these hardware features to accelerate hardware configuration and application development.
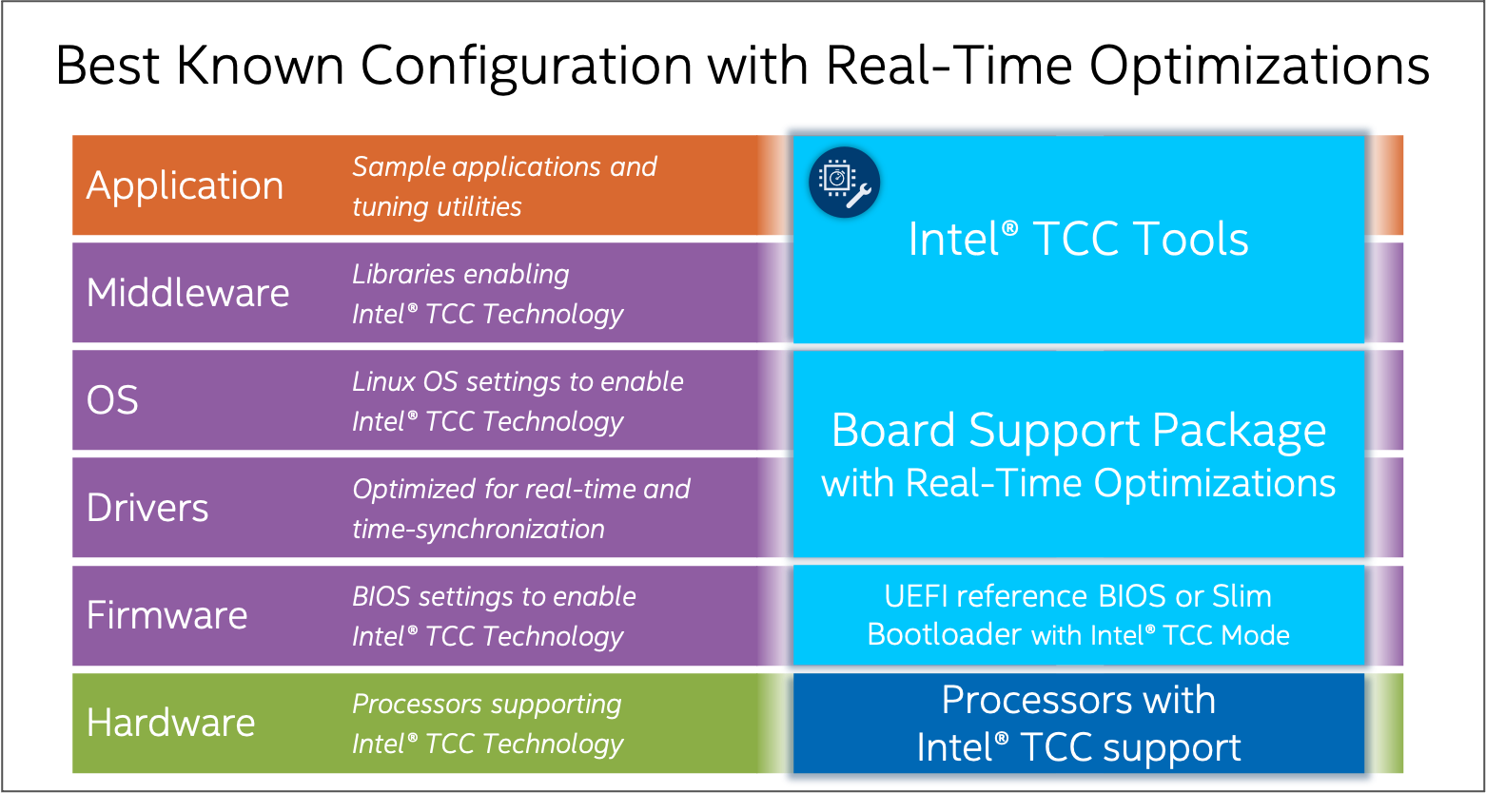
The stack consists of:
Real-time hardware: Intel Atom® and Intel® Core™ processors, optimized for real-time applications (list of supported processors)
System software:
Linux OS: Yocto Project*-based board support package (BSP) with real-time optimizations, also referred to as PREEMPT_RT or RT kernel
Linux OS: Debian Buster with real-time optimization, also referred to as PREEMPT_RT kernel.
ACRN Real Time Hypervisor.
UEFI reference BIOS with Intel TCC Mode
Intel TCC Tools (this product)
Why Intel TCC Tools?¶
System software optimizations can satisfy many real-time use cases
System software has the highest impact on real-time performance. The BSP and UEFI reference BIOS contain optimizations such as Linux kernel build configuration settings and boot parameters, power management settings, and Intel TCC Mode, that help drastically decrease execution latencies and reduce jitter, at times up to several orders of magnitude. System software optimizations, when used with target processors are sufficient to satisfy real-time use cases with a broad range of cycle times for the most common real-time applications.
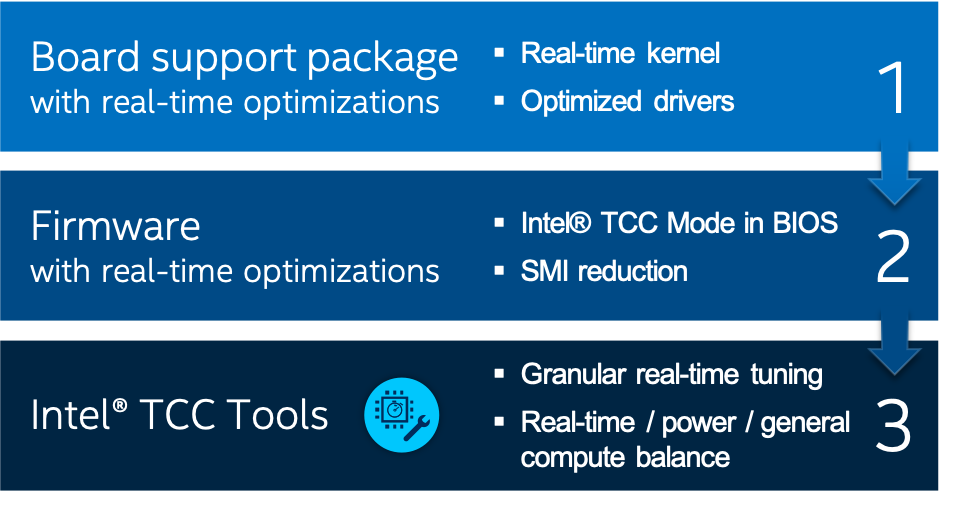
System software optimizations may be all you need to meet your real-time requirements. To learn more about system software tuning, the BSP, and Intel TCC Mode in BIOS, see the Real-Time Tuning Guide 11th Generation Intel® Core, and Real-Time Tuning Guide Atom® x6000E Series for your target processor.
Intel TCC Tools allow for use case-specific optimizations
For some use cases, meeting real-time requirements is not enough. Some must be mindful of system power consumption or residual compute capabilities for data processing or graphical UI. Optimizing only system software may not be sufficient in these cases. For example, enabling Intel TCC Mode has a strong impact on system power consumption which might not be acceptable.
Optimizations to address the unique demands of some real-time applications or further decrease cycle times require more granular use of Intel TCC features and special tuning techniques, such as advanced cache management and I/O fabric tuning.
Such granular tuning, if unassisted, requires special knowledge of processor architecture including the intricacies of a particular microarchitectural generation which is unattainable and unnecessary information for the majority of developers. Intel TCC Tools facilitates these techniques by offering C application programming interfaces (APIs) and tools.
Furthermore, tuning is usually preceded by debugging and bottlenecks identification that involves measurement. Given the nature of real-time applications and their latency sensitivities, conventional measurement tools may not be precise enough and induce overhead impacting measurement results. Latency measurement offered by Intel TCC Tools is free of these limitations and offers high precision while being minimally intrusive.
For information on using and developing with Intel TCC Tools, refer to the Developer Guide
Note: If you do not have access to the Developer Guide, contact your Intel representative for assistance with accessing Intel TCC Tools.
Intel TCC Tools - Resources¶
Intel TCC Tools is an independent product. For help and support with Intel TCC Tools, refer to the following:
Intel TCC Tools - Prerequisites¶
Complete the following steps to prepare Intel TCC Tools.
Verify that the target system (where ECI will be installed) contains a TCC Tools compatible BIOS. Refer to the table below for supported BIOS versions:
Note
If your BIOS is not compatible, contact your Intel representative for assistance.
The Vecow Tiger Lake (Vecow TGL) system does not have a BIOS for TCC 2021.3. The BIOS being used for Vecow Tiger Lake is based on the 2021.1 BIOS referenced below. Vecow Tiger Lake BIOS is referenced from ‘TGLIFUI1.R00.3455.A02.2011240812’.
System
BIOS for TCC 2021.3
EHL-CRB
EHLSFWI1.R00.3273.A04.2107240322
TGL-RVP
TGLIFUI1.R00.4304.A01.2107200604
Vecow TGL
E5000XXU3FRT103
System
BIOS ACRN TGL RVP
TGL-RVP
TGLIFUI1.R00.4304.A01.2107200604 (Specifically requires TSN)
Configure the target system BIOS according to the table below. Note: Select the tab corresponding to your target system CPU.
Go to Intel(R) Advanced Menu > Intel(R) Time Coordinated Computing(R) on the target system and configure the BIOS as listed in the following table:
Setting Name
Option
Intel(R) TCC Mode
Enabled
Intel(R) TCC Authentication
Disabled
For Tiger Lake, go to Intel(R) Advanced Menu > Intel(R) Time Coordinated Computing and configure the BIOS as listed in the following table:
Setting Name
Option
Intel(R) TCC Mode
Enabled
Intel(R) TCC Authentication
Disabled
Software SRAM
Enabled
Data Streams Optimizer
Enabled
Locate the Intel TCC Tools offline host system installer script in the ECI release package at the following directory:
└── Support └── Time-Coordinated-ComputingThis script will be used in later steps.
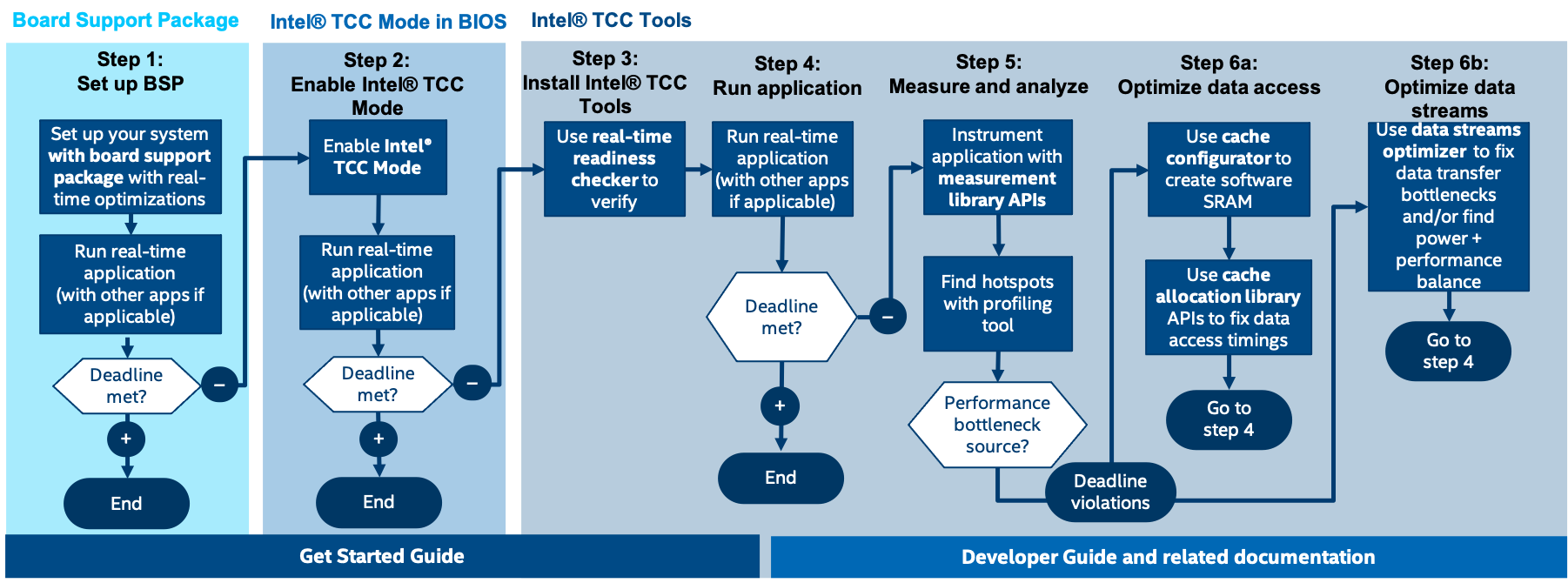
Familiarize yourself with the Intel TCC Tools Get Started Guide.
Note: The TCC Tools Get Started Guide informs the user to build and install a Yocto image. Since these steps have already been completed by ECI, please skip them: Step 1: Build Yocto Project-Based Image and Step 5: Install on Target.
Intel TCC Tools - Enabling Drivers and SSRAM(With and Without ACRN)¶
The methods to enable Intel TCC Tools vary depending on if the ACRN Hypervisor is present. If the ECI image you are using contains the ACRN Hypervisor, select the ECI with ACRN tab. Otherwise, select the ECI without ACRN tab.
After completing this section, you will have enabled the TCC Software SRAM buffer, updated the TCC cache BIOS subregion via a firmware update mechanism, and verified the system configuration.
The following section is applicable to:

Make sure that the Intel TCC Tools - Prerequisites section has been completed.
Download a prebuilt ECI image, or build an ECI image with the
Intel® Time Coordinated Computingfeature. For more information, refer to Building ECI Targets.
Install the ECI image to a target system. For more information, refer to Installing ECI Images.
Login to the target system. On Debian-based images, reconfigure the
fwupdatepackage and prepare the bootloader by performing the following commands:$ dpkg-reconfigure fwupdate $ cp /boot/efi/EFI/BOOT/bootx64.efi /boot/efi/EFI/BOOT/grubx64.efi
The following setup will activate a pre-defined configuration for the Software SRAM. This includes:
Enabling the TCC Driver to be auto-loaded
Creating BIOS capsules with the updated cache configuration, which will be deployed to the BIOS sub-regions when the system is re-booted.
Configure the Software SRAM buffer by performing the command below. Select the tab corresponding to your target system.
$ /usr/share/tcc_tools/scripts/setup_ssram_v1/tcc_setup_ssram.sh enable
$ /usr/share/tcc_tools/scripts/setup_ssram/tcc_setup_ssram.sh enable
$ /usr/share/tcc_tools/scripts/setup_ssram/tcc_setup_ssram.sh enable --cpu atom
The target system will reboot twice during the BIOS update process. Do not interrupt this process. On the first reboot, the BIOS will locate and load the capsules, as shown in the figure below:
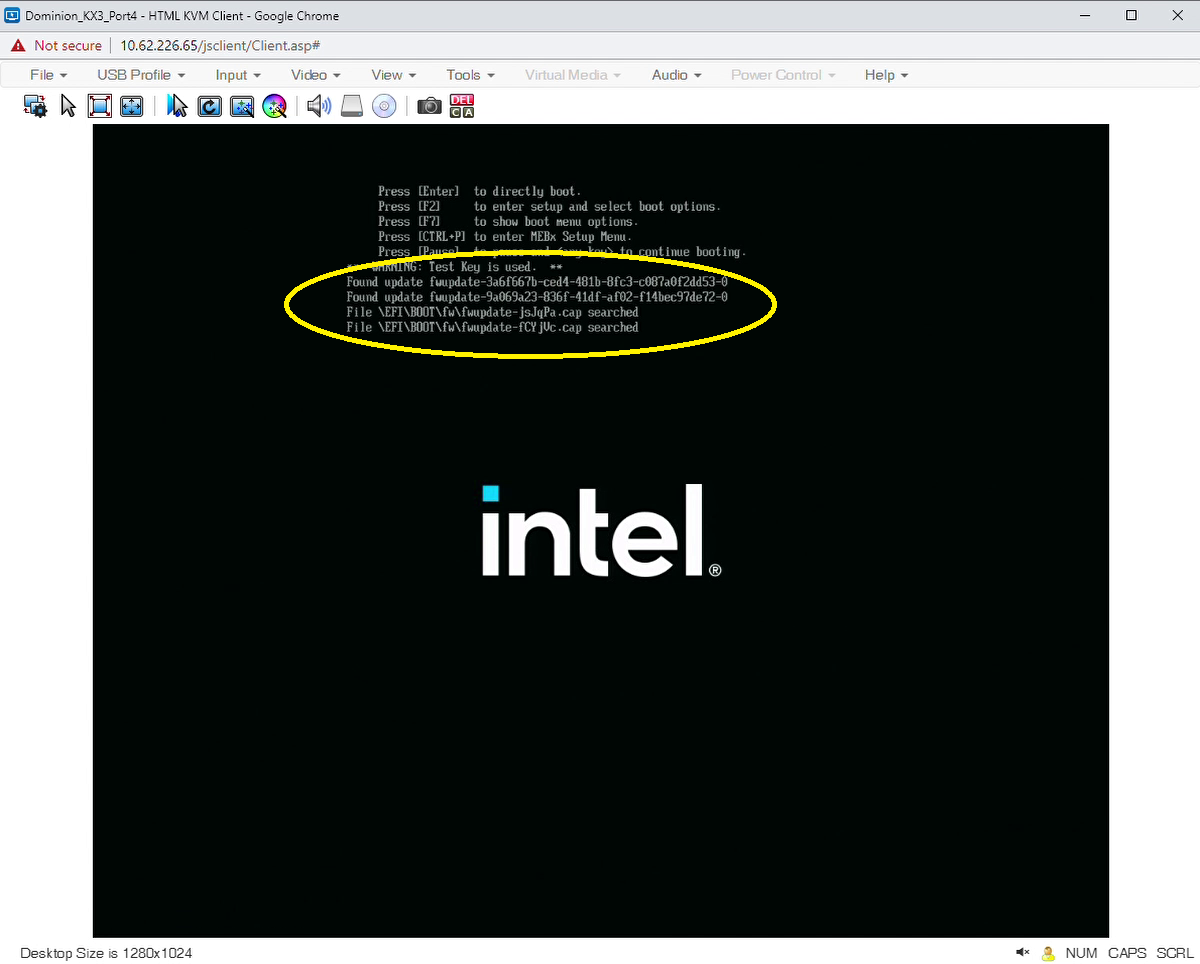
On the second reboot, the BIOS will apply the capsules. Typically a progress bar appears during this process, as shown in the figure below:
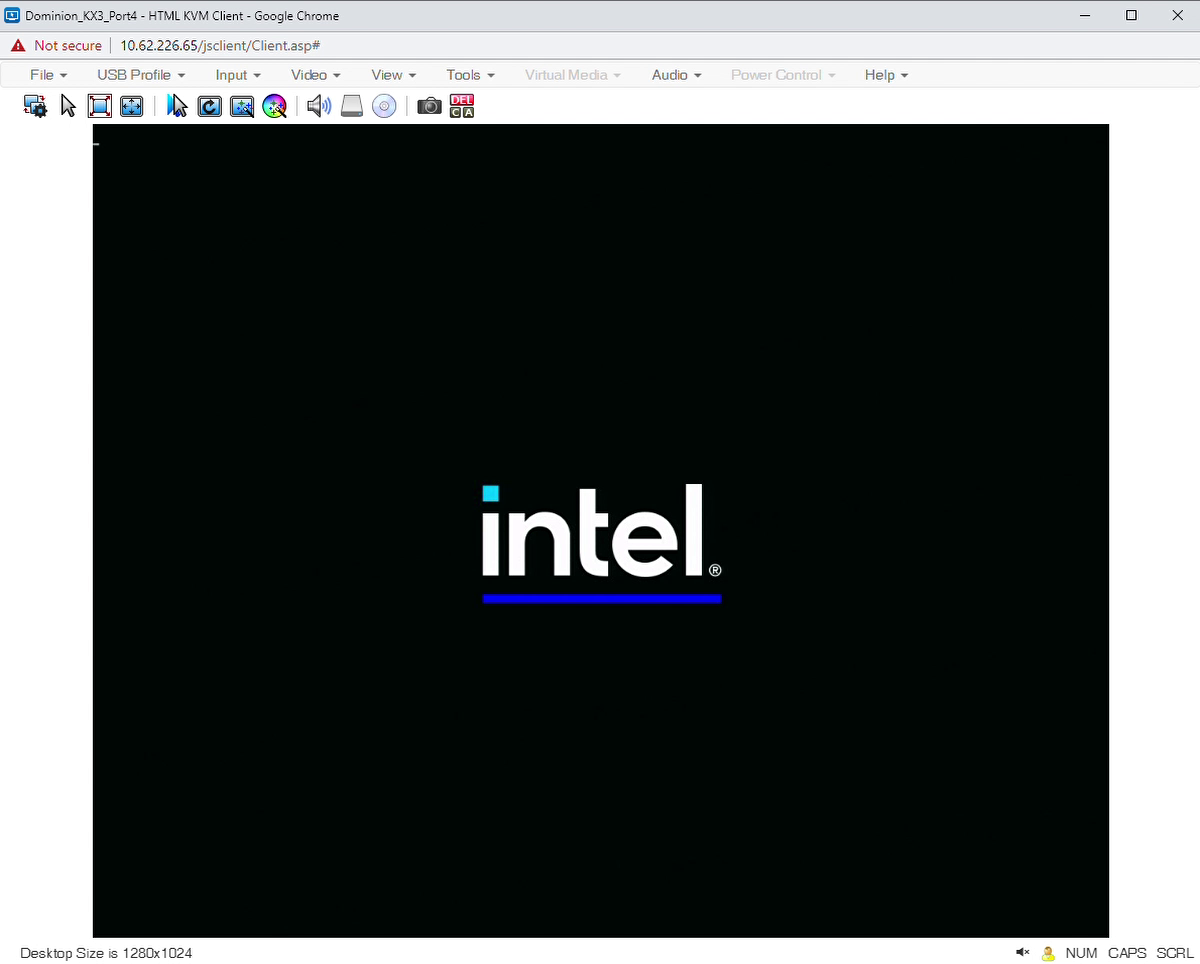
After the target system has fully booted, login again. Verify the system configuration by performing the command below. Select the tab corresponding to your target system.
$ /usr/share/tcc_tools/scripts/setup_ssram_v1/tcc_setup_ssram.sh enable --verify
$ /usr/share/tcc_tools/scripts/setup_ssram/tcc_setup_ssram.sh enable --verify
$ /usr/share/tcc_tools/scripts/setup_ssram/tcc_setup_ssram.sh enable --cpu atom --verify
The script verifies whether the TCC Driver is loaded and if the RTCT table, found at
/sys/firmware/acpi/tables/PTCT, complies with the pre-defined Software SRAM configuration. If everything is correct, the script will output the following:verify [ENABLED ] Driver [ENABLED ] Driver auto-load [VALID ] Cache configuration (from RTCT) SYSTEM CONFIGURATION IS CORRECT
Decode the RTCT table and verify that it contains an active Software SRAM configuration by performing the following command:
$ tcc_cache_info_read | grep -C 8 SoftwareSRAM
If the pre-defined Software SRAM configuration is active, this command should report three records with Software SRAM buffers:
{ "Level": 2, "Cache_ID": 2, "Base": 1074266112, "Size": 262144, "Shared": 0, "Type": "common.rtct.v2.rtct.SoftwareSRAM" }, { "Level": 2, "Cache_ID": 3, "Base": 1074528256, "Size": 262144, "Shared": 0, "Type": "common.rtct.v2.rtct.SoftwareSRAM" }, { "Level": 3, "Cache_ID": 0, "Base": 1074266112, "Size": 1048576, "Shared": 0, "Type": "common.rtct.v2.rtct.SoftwareSRAM" },
If all verification steps pass then Intel TCC Tools is ready to use. Refer to section Intel TCC Tools - Cache Configurator for information on configuring the system cache to work best with real-time workloads.
The section will help you set up Intel TCC with the ACRN Hypervisor. The following figure illustrates the procedure to enable Intel TCC on an ACRN virtual machine (VM).
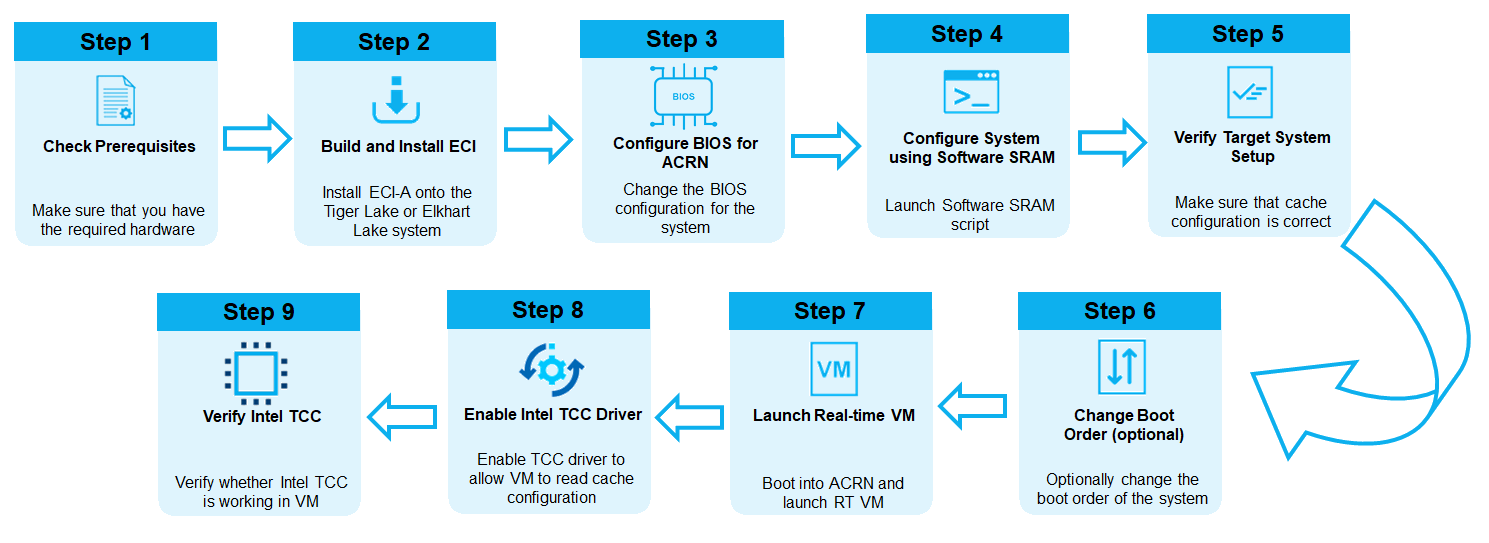
After completing this section, you will have enabled the TCC Software SRAM buffer, updated the TCC cache BIOS subregion via a firmware update mechanism, started a real-time VM, and verified the system configuration.
The following section is applicable to:

- Step 1: Check the Prerequisites
Make sure that the Intel TCC Tools - Prerequisites section has been completed.
- Step 2: Build and Install ECI
Download a prebuilt ACRN variant ECI image, or build an ACRN variant ECI Use Case. Note: The ACRN variants of prebuilt ECI images and ECI Use Cases contain ACRN and an embedded ECI VM with TCC features enabled.
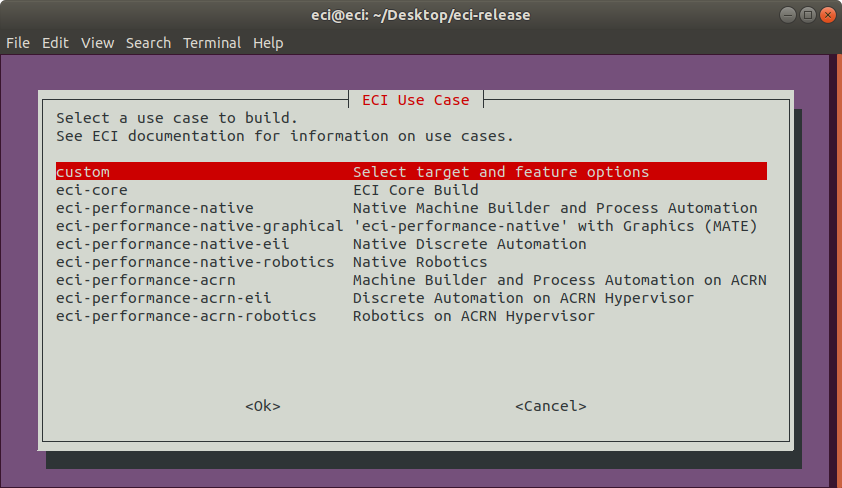
Install the ECI-A image to a target system. For more information, refer to Installing ECI-A.
- Step 3: Configure BIOS for ACRN with Intel TCC
If not done earlier, change the BIOS configuration of the system. This will allow ECI-A to boot up correctly, enable Intel TCC, and also provide the capability to launch a RT VM.
Boot the target system and access the BIOS (typically pressing the delete or F2 keys while booting will open the BIOS menu).
Refer to section Configure Target System BIOS to configure the BIOS for ACRN
Refer to section Intel TCC Tools - Prerequisites to configure the BIOS for Intel TCC Tools.
Save the changes.
- Step 4: Configure System using Software SRAM
The following setup will activate a pre-defined configuration for the Software SRAM. This includes:
Enabling the TCC Driver to be auto-loaded
Creating BIOS capsules with the updated cache configuration, which will be deployed to the BIOS sub-regions when the system is re-booted.
Reboot the target system. From the GRUB boot option menu, select Linux and then press Enter.
Login to the target system and configure the Software SRAM buffer by performing the command below. Select the tab corresponding to your target system.
$ /usr/share/tcc_tools/scripts/setup_ssram_v1/tcc_setup_ssram.sh enable
$ /usr/share/tcc_tools/scripts/setup_ssram/tcc_setup_ssram.sh enable
$ /usr/share/tcc_tools/scripts/setup_ssram/tcc_setup_ssram.sh enable --cpu atom
The target system will reboot twice during the BIOS update process. Do not interrupt this process. On the first reboot, the BIOS will locate and load the capsules, as shown in the figure below:

On the second reboot, the BIOS will apply the capsules. Typically a progress bar appears during this process, as shown in the figure below:

- Step 5: Verify Target System Setup
After the target system has rebooted and displays the GRUB boot option menu, select Linux and then press Enter.

After the target system has fully booted, login again. Verify the system configuration by performing the command below. Select the tab corresponding to your target system.
$ /usr/share/tcc_tools/scripts/setup_ssram_v1/tcc_setup_ssram.sh enable --verify
$ /usr/share/tcc_tools/scripts/setup_ssram/tcc_setup_ssram.sh enable --verify
$ /usr/share/tcc_tools/scripts/setup_ssram/tcc_setup_ssram.sh enable --cpu atom --verify
The script verifies whether the TCC Driver is loaded and if the RTCT table, found at
/sys/firmware/acpi/tables/PTCT, complies with the pre-defined Software SRAM configuration. If everything is correct, the script will output the following:verify [ENABLED ] Driver [ENABLED ] Driver auto-load [VALID ] Cache configuration (from RTCT) SYSTEM CONFIGURATION IS CORRECT
Decode the RTCT table and verify that it contains an active Software SRAM configuration by performing the following command:
$ tcc_cache_info_read | grep -C 8 SoftwareSRAM
If the pre-defined Software SRAM configuration is active, this command should report three records with Software SRAM buffers:
{ "Level": 2, "Cache_ID": 2, "Base": 1074266112, "Size": 262144, "Shared": 0, "Type": "common.rtct.v2.rtct.SoftwareSRAM" }, { "Level": 2, "Cache_ID": 3, "Base": 1074528256, "Size": 262144, "Shared": 0, "Type": "common.rtct.v2.rtct.SoftwareSRAM" }, { "Level": 3, "Cache_ID": 0, "Base": 1074266112, "Size": 1048576, "Shared": 0, "Type": "common.rtct.v2.rtct.SoftwareSRAM" },
- Step 6: Change Boot Order
You can optionally change the boot order of the system. This will reduce the need to enter BIOS to boot from a specific device. Using the following example, you can control the boot order of your system.
After verifying whether the Software SRAM capsule has been applied correctly, you can remove the
RTCMboot option as it is not required anymore. Run the following command:#Replace '<bootnum>' with the number corresponding to "RTCM". Example has been provided below. efibootmgr -b <bootnum> -B
root@eci-intel-0faa:~# efibootmgr BootCurrent: 0006 Timeout: 5 seconds BootOrder: 0006,0005,0004,0001,0002,0000,0003 Boot0000* Enter Setup Boot0001* Internal UEFI Shell Boot0002* Boot Device List Boot0003* UEFI SanDisk Extreme 4C530001091014102431 Boot0004* UEFI Samsung SSD 970 EVO Plus 500GB S58SNJ0N610041M 1 Boot0005* ECI Boot0006* RTCM root@eci-intel-0faa:~# efibootmgr -b 0006 -B BootCurrent: 0006 Timeout: 5 seconds BootOrder: 0005,0004,0001,0002,0000,0003 Boot0000* Enter Setup Boot0001* Internal UEFI Shell Boot0002* Boot Device List Boot0003* UEFI SanDisk Extreme 4C530001091014102431 Boot0004* UEFI Samsung SSD 970 EVO Plus 500GB S58SNJ0N610041M 1 Boot0005* ECI
- Step 7: Launch Real-time VM
Boot into the ECI-A ‘ACRN’ boot option and launch a RT VM.
After validating the system, reboot the system. When the GRUB menu appears, let the system boot normally. The ACRN option will be selected, by default.
Login to the ACRN service OS and perform the following command to launch the RT VM:
$ /var/lib/machines/scripts/launch-rtvm.sh
- Step 8: Enable Intel TCC Driver
Enable
tcc_driver. This will allow the VM to read the cache configuration.The boot up of RT VM will take couple minutes and will give you a login console. The login for VM is
root. Once the console is available, run the following command to enable the Intel TCC Driver:$ /usr/share/tcc_tools/scripts/setup_ssram/control_tcc_driver.sh enable
- Step 9: Verify Intel TCC on ACRN VM
Run the
tcc_cache_allocation_sampleto verify whether Intel TCC is correctly working on the VM.Once the driver is enabled, perform the following commands to run the Intel TCC example:
$ export TCC_LOG_LEVEL=INFO $ tcc_cache_allocation_sample --collect --latency 50 --stress --cpuid 1
The expected output should be similar to the following:
Running with arguments: latency = 50 ns, stress = internal, iterations = 100, collector = libtcc_collector.so, mask interrupts = true : print_regions_table | Available regions: print_regions_table | Id Cache level Latency, ns Affinity mask Entire region size, b Allocation size from tcc.config, b print_regions_table | 4294967295 TCC_MEM_DRAM 114 11000000 Regular RAM Regular RAM print_regions_table | 2 TCC_MEM_L3 49 11000000 524288 262144 print_regions_table | 0 TCC_MEM_L2 6 10000000 262144 98304 print_regions_table | 1 TCC_MEM_L2 6 01000000 262144 98304 Allocating memory according to the latency requirements allocators_manager_get_next | Searching for memory to satisfy requirements: latency=50 ns, affinity=01000000 allocators_manager_get_next | Found suitable allocator for request: region #1 (TCC_MEM_L3) region_allocator_malloc | Calling region malloc with: size=97280 Running workload. This may take a while, depending on sleep and iteration values Deallocating memory *** Statistics for workload **************************** Minimum total latency: 21898 CPU cycles (7811 ns) Maximum total latency: 24051 CPU cycles (8579 ns) Average total latency: 22703 CPU cycles (8098 ns) Minimum latency per buffer access: 43 CPU cycles (15 ns) Maximum latency per buffer access: 47 CPU cycles (16 ns) Average latency per buffer access: 44 CPU cycles (15 ns) ********************************************************
Intel TCC Tools - Cache Configurator¶
In the previous sections, you set up a pre-defined Software SRAM configuration. The pre-configured BIOS capsules with this Software SRAM configuration was deployed into the BIOS sub-regions as described the Intel® TCC Get Started Guide (Complete Target Setup of Software SRAM). The pre-defined Software SRAM configuration consists of three buffers:
One buffer located in L3 cache guaranteeing a maximum latency of 49 ns.
Two buffers located in L2 cache and guaranteeing a maximum latency of 6 ns.
While this pre-defined Software SRAM configuration represents only an example configuration, you can use the TCC Cache Configurator to create your own Software SRAM configurations and to deploy those onto the target board.
For more information on the working of the TCC Cache Configurator, refer to Cache Configurtor.
The following steps, which provide a practical guide on how to use the cache configurator, correspond to Launch the Cache Configurator of the Intel® TCC Tools 2021.2 Developer Guide.
Prepare Target¶
Enable the tcc_buffer driver (if it is not enabled already):
$ cd /usr/share/tcc_tools/scripts/setup_ssram/control_tcc_driver.sh
Run TCC Cache Configurator¶
On the TCC Tools host machine, launch the TCC Cache Configurator. You will need to update the sample environment with the correct values for your Tiger Lake machine.
Follow the steps in TCC Cache Configurator to set up cache configuration for the Tiger Lake system.
Intel TCC Tools - Sanity Checks¶
Run these sanity checks to make sure that the TCC tool is working.
Sanity Check 1: RT Checker¶
Intel TCC system hardware RT checker is a tool to make sure that the system is ‘RT READY’.
Run RT checker:
$ /usr/bin/tcc_rt_checkerThis will compare your current BIOS configuration with the best known configuration. If there is a mismatch, the message “NOT RT READY” will be displayed in red right next to it. You need to go into the BIOS and change the setting to the value provided by the output. After making all changes, rerun the RT checker executable to make sure system is ‘RT READY’.
Sanity Check 2: Verify TCC Drivers and Software SRAM¶
After configuring TCC (see section Intel TCC Tools - Enabling Drivers and SSRAM(With and Without ACRN)), verify the system configuration by performing the command below. Select the tab corresponding to your target system.
$ /usr/share/tcc_tools/scripts/setup_ssram_v1/tcc_setup_ssram.sh enable --verify
$ /usr/share/tcc_tools/scripts/setup_ssram/tcc_setup_ssram.sh enable --verify
$ /usr/share/tcc_tools/scripts/setup_ssram/tcc_setup_ssram.sh enable --cpu atom --verify
The script verifies whether the TCC Driver is loaded and if the RTCT table, found at
/sys/firmware/acpi/tables/PTCT, complies with the pre-defined Software SRAM configuration. If everything is correct, the script will output the following:verify [ENABLED ] Driver [ENABLED ] Driver auto-load [VALID ] Cache configuration (from RTCT) SYSTEM CONFIGURATION IS CORRECT
Troubleshooting¶
Cache Configuration is INVALID
If the cache configuration is INVALID, it means that the capsules have not been applied to the BIOS sub-regions. In most cases, this occurs if the system does not reboot appropriately and you have to run a power-off/power-on cycle. If the cache configuration is INVALID, repeat the steps listed in Intel TCC Tools - Enabling Drivers and SSRAM(With and Without ACRN).
Only Driver is Disabled
If only the Driver is disabled, run the following command to enable it:
$ cd /usr/share/tcc_tools/scripts/setup_ssram/control_tcc_driver.sh enable
If the above command does not work, run the following command to enable the driver (you need to rerun the command if the system is rebooted):
$ modprobe tcc_buffer .. code-block:: console +-----+------------------+------------------+------------------+--------------+ | Num | Checker name | Description | Note | Result | +-----+------------------+------------------+------------------+--------------+ | 1 | Hypervisor | Checks that the | Hypervisor is on | NA | | | detection | system was run | | | | | | from hypervisor | | | +-----+------------------+------------------+------------------+--------------+ | 2 | RTCM Checker | Checks that RTCM | Can't check | FAILED | | | | is enabled | current boot | | +-----+------------------+------------------+------------------+--------------+ | 3 | Real-time | Checks that | Real-time | NA | | | configuration | Real-time | configuration | | | | driver Checker | configuration | driver does not | | | | | driver exists | exist | | +-----+------------------+------------------+------------------+--------------+ | 4 | RT Kernel | Checks that RT | Current kernel | RT_READY | | | Checker | kernel is used | is RT | | +-----+------------------+------------------+------------------+--------------+ | 5 | GT CLOS Checker | Checks that GPU | Failed to check | FAILED | | | | doesn't overlap | GT CLOS due to | | | | | with dedicated | There is no | | | | | L3 CPU CLOS | corresponding | | | | | | SSRAM_WayMask | | | | | | entry for SSRAM | | | | | | SoftwareSRAM(Lev | | | | | | el=2, | | | | | | Cache_ID=0, | | | | | | Base=2130706432, | | | | | | Size=131072, | | | | | | Shared=0, Type=' | | | | | | common.rtct.v2.r | | | | | | tct.SoftwareSRAM | | | | | | ') | | +-----+------------------+------------------+------------------+--------------+ | 6 | Linux Kernel's | Checks that all | Cmdline | NON_RT_READY | | | command-line | kernel's | parameters that | | | | parameters | command-line par | are missing:art= | | | | Checker | ametersrequired | virtallow | | | | | for real-time | idle=poll rcupda | | | | | workload are set | te.rcu_cpu_stall | | | | | | _suppress=1 | | | | | | mce=off | | | | | | hpet=disable num | | | | | | a_balancing=disa | | | | | | ble | | | | | | igb.blacklist=no | | | | | | efi=runtime | | | | | | hugepages=1024 i | | | | | | 915.force_probe= | | | | | | * i915.enable_rc | | | | | | 6=0 | | | | | | i915.enable_dc=0 | | | | | | i915.disable_pow | | | | | | er_well=0 | | | | | | rcu_nocb_poll | | | | | | isolcpus=<list> | | | | | | rcu_nocbs=<list> | | +-----+------------------+------------------+------------------+--------------+ Real-time BIOS capabilities checkers: +-----+------------------+------------------+------------------+--------------+ | Num | Checker name | Description | Note | Result | +-----+------------------+------------------+------------------+--------------+ | 1 | Enhanced Intel | Checks that | Enhanced Intel | RT_READY | | | SpeedStep(R) | Enhanced Intel | SpeedStep(R) | | | | Technology | SpeedStep(R) | Technology is | | | | | Technology is | disabled | | | | | disabled | | | +-----+------------------+------------------+------------------+--------------+ | 2 | Intel(R) Speed | Check that | Intel(R) Speed | RT_READY | | | Shift Technology | Intel(R) Speed | Shift Technology | | | | | Shift Technology | is disabled | | | | | is disabled | | | +-----+------------------+------------------+------------------+--------------+ | 3 | Low Power S0 | Check that Low | Error in ACPI | FAILED | | | Idle Capability | Power S0 Idle is | table reading | | | | | disabled | | | +-----+------------------+------------------+------------------+--------------+ | 4 | CPU PCI Express | Check that CPU | | RT_READY | | | ASPM | PCI Express ASPM | | | | | | is disabled | | | +-----+------------------+------------------+------------------+--------------+ | 5 | Intel(R) Hyper- | Checks that | Intel(R) | RT_READY | | | Threading | Intel(R) | Hyperthreading | | | | Technology | Hyperthreading | Technology is | | | | | Technology is | disabled | | | | | disabled | | | +-----+------------------+------------------+------------------+--------------+ | 6 | Cache Allocation | Checks that | Cache Allocation | NON_RT_READY | | | Technology | Cache Allocation | Technology (CAT) | | | | | Technology is | is not supported | | | | | enabled | | | +-----+------------------+------------------+------------------+--------------+ | 7 | Cache Allocation | Checks that CAT | L3 CAT is | RT_READY | | | Technology | capabilities are | unsupported. L2 | | | | capabilities | enabled | CAT is | | | | | | unsupported. | | | | | | Memory Bandwidth | | | | | | Allocation (MBA) | | | | | | is unsupported. | | +-----+------------------+------------------+------------------+--------------+ | 8 | #AC Split Lock | When enabled, | #AC Split Lock | RT_READY | | | | generates an | is disabled | | | | | Alignment Check | | | | | | Exception when | | | | | | an application | | | | | | attempts to | | | | | | issue a split | | | | | | lock because a | | | | | | split lock | | | | | | increases | | | | | | latency. | | | +-----+------------------+------------------+------------------+--------------+